Cybersecurity: a new challenge for the European manufacturing industry
Europe is creating a regulatory framework that will have a significant impact on strategic sectors such as capital goods
Stefano Lugli and Stefano Nicolussi (UCIMA Technical Service)
The European manufacturing sector is undergoing a profound transformation, driven not only by the introduction of innovative technologies but also by the adoption of new regulations that will affect the safety and efficiency of products and company networks.
With the introduction of the NIS2 Directive, the Cyber Resilience Act, the AI Act, the Data Act and the new Machinery Regulation, Europe is creating a regulatory framework that will have a significant impact on strategic sectors such as capital goods. In the short and medium term, these legislative measures will affect security, competitiveness and innovation of capital goods companies in terms of both products and organisational structures.
According to the Clusit 2024 report on cyberattacks, manufacturing remains by far the most targeted sector in Italy.
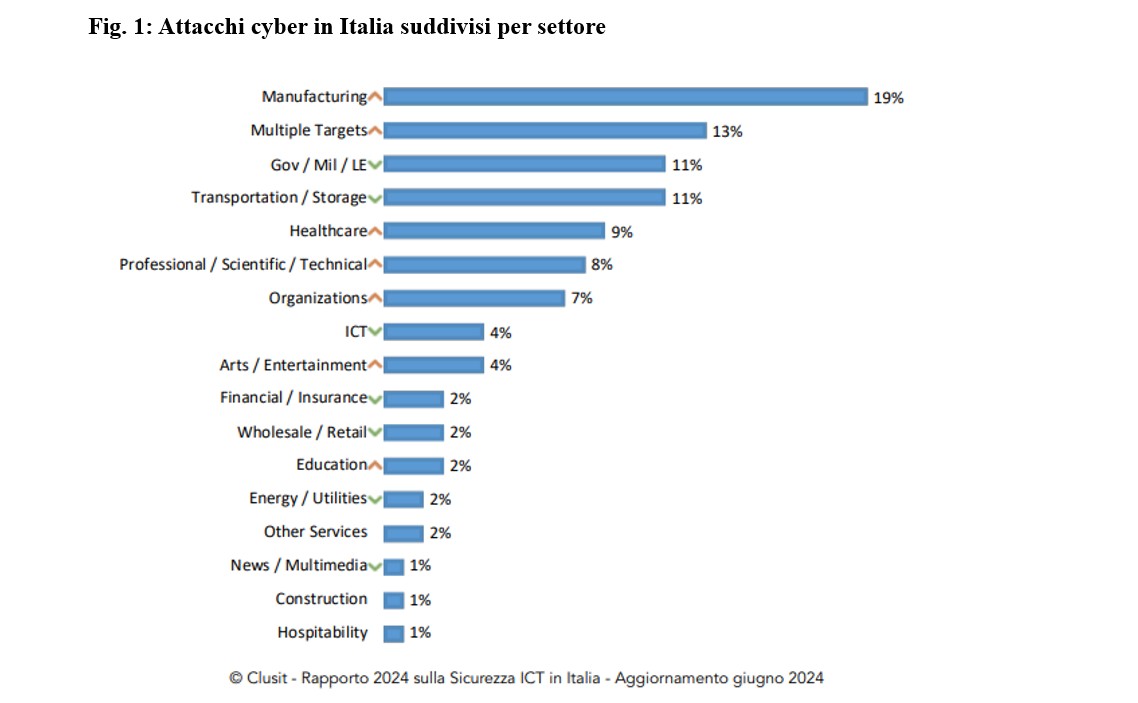
As the report reveals, this distribution differs significantly from the global sample, where the manufacturing sector accounts for just 5% of incidents (ranking seventh). In addition, more than a quarter (28%) of all cyber incidents targeting the manufacturing industry worldwide involve Italian companies.
Italian and European businesses are increasingly exposed to new vulnerabilities and risks, including:
- loss of sensitive data
- theft of intellectual property, industrial secrets, production data, etc.
- various types of fraud and business interruptions
all of which can have devastating economic and legal consequences, as well as causing severe reputational damage.
The same concerns are evident in the United States, where the introduction of the 2023 National Electrical Code includes specific cybersecurity measures and requirements relating to capital goods. Moreover, a review of the latest technical specifications requested by clients from technology suppliers shows that cybersecurity is an increasingly prominent factor, with some customers even requiring specific certifications.
For exporter companies worldwide, the cybersecurity of products and networks is a long-term challenge and will become an increasingly strategic competitiveness factor.
It is also worth noting that cybersecurity is one of the key enabling technologies of Industry 4.0. As connectivity and data exchange expand, the need to protect critical industrial systems and production lines from cyber threats has never been greater.
This article will examine the issue from the perspective of enterprise networks, focusing on the new NIS 2 Directive which is currently being implemented across Europe.
NIS 2 in detail and its impact on the packaging industry
The goal of the NIS 2 Directive is to strengthen the security of IT systems across the European Union and to ensure a high level of cybersecurity and cyber resilience by fostering a culture of cybersecurity within strategic companies and organisations. This will be achieved by enhancing the protection of digital networks and infrastructures, which include technologies, applications, data and processes used by businesses, public bodies and essential service operators.
The NIS 2 Directive applies mandatorily to European public and private organisations operating in 11 sectors classified as “essential” and an additional 7 classified as “important”, as outlined in the annexes to the directive (Directive 2022/2555).
Mid-size or large machinery and equipment manufacturers (as defined by the EU in terms of employee numbers and turnover) are classified as “important” entities and have been defined by the European Union as a strategic sector in which easy security breaches cannot be permitted.
Under NIS 2, certain sectors (such as the chemical, food and pharmaceutical industries) that in some cases are customers of packaging technology produced by ACIMAC member companies are also classified as essential or important, with the specific implications regarding the security measures to be adopted towards the entire supply chain, as set out below.
Plant and machinery suppliers for packaging are required to meet exceptionally stringent standards, adopt rigorous risk assessment and monitoring protocols and adhere to precise reporting obligations in the event of a cyber incident. In other words, the directive requires mid-size and large packaging technology companies to implement risk management strategies and ensure the security of industrial systems, including their supply chains.
Application of NIS 2 in Italy and Europe
Legislative Decree 138/2024, which transposed the NIS 2 Directive into Italian law, has been in force since 18 October 2024, fully aligning with the timeframe set by the European directive.
However, some countries are lagging behind in the transposition process.
The first fundamental step, which in Italy was completed on 28 February, was the mandatory registration of NIS 2 obligated entities on the portal of the national supervisory authority (in Italy, the National Cybersecurity Agency ACN).
Once registration is confirmed, companies must comply with the various obligations within a specific timeframe.
As of January 2026, essential and important entities must notify ACN without undue delay of any incident that significantly impacts the provision of their services. Within 24 hours, a pre-notification must be sent, followed by a formal incident notification within 72 hours, which must specify whether the incident resulted from unlawful or malicious acts or has cross-border implications.
Essential and important entities also have downstream reporting obligations. When deemed appropriate and feasible, and after consulting with ACN, they must promptly inform the users of their services at risk of a significant cyber threat of any corrective or mitigation measures they can take in response.
Additionally, after consulting with ACN and where considered appropriate, essential and important entities must inform these recipients of the nature of the cyber threat.
In cases where a threat may extend to client companies (for example via installed machinery), suppliers must carefully assess how the risk could extend to their customers.
To meet these requirements, companies must adopt the following:
• Incident response plan: develop and maintain a plan describing the phases of detection, containment, eradication and recovery.
• Incident log: document and analyse each incident to determine its root cause and prevent future occurrences.
• Incident management team: create and train a dedicated response team capable of promptly addressing incidents.
The most critical and challenging requirement, however, will involve the complete adoption of all technical measures outlined in Article 24 of Legislative Decree 138/2024 on IT security risk management by September 2026. This set of ten actions and activities (see Fig. 2) consists of a series of adequate and proportionate technical, operational and organisational measures designed to prevent or minimise the impact of cyber incidents on service recipients and other related services. These measures must follow a multi-risk approach to protect information and network systems, as well as their physical environments, from cyber threats. Key elements include risk analysis policies and IT and network security protocols. Here too, compliance will rely on an effective, transparent and professional preventive risk analysis procedure.
The ten areas of application of security measures
• Risk analysis and IT system security policies
• Security of acquisition, development and maintenance [...], including vulnerability management and disclosure
• Incident management
• Policies and procedures for evaluating the effectiveness of cybersecurity risk management measures
• Human resource security, access control strategies and asset management
• Business continuity, including backup management and disaster recovery, and crisis management
• Basic cyber hygiene practices and cybersecurity training
• Use of multi-factor or continuous authentication systems and secure communication systems
• Supply chain security, including aspects relating to the security of relationships with direct suppliers or service providers
• Policies and procedures relating to the use of encryption and, where appropriate, cryptography
A crucial aspect of NIS 2 compliance concerns supply chain security, including the cybersecurity measures governing relationships between entities and their direct suppliers or service providers. The directive states: “…when considering which measures are appropriate, entities shall take into account the vulnerabilities specific to each direct supplier and service provider and the overall quality of products and cybersecurity practices of their suppliers and service providers, including their secure development procedures.”
This means that technology suppliers must conduct a thorough risk assessment across the entire supply chain, including those of smaller companies that, while not directly obligated under NIS 2, must still implement the directive’s technical measures under contractual agreements imposed by NIS 2-obligated entities. In other words, these suppliers must comply with the cybersecurity requirements determined by their NIS 2-obligated clients based on prior risk analyses.
Companies should therefore prepare for:
• Adoption of supplier evaluation tools: establishing security criteria for selecting and assessing suppliers.
• Contractual clauses: contracts should include security requirements and reporting responsibilities in the event of an incident.
• Continuous monitoring: conducting periodic checks to ensure that suppliers comply with agreed security standards.
NIS 2-obligated entities could also include NIS 2 machinery manufacturers that integrate third-party products into their own supplies, as well as customers in previously listed sectors (chemicals, food, etc.) that are classified under NIS 2.
These evaluations may also be conducted by machinery manufacturers’ clients to ensure the cybersecurity compliance of the services and products they procure, given their potential exposure to cyber threats.
Penalties for non-compliance
While the directive’s intent (encouraging preventive measures and ensuring companies implement appropriate cybersecurity protocols) is highly commendable, the penalty framework for non-compliance appears excessively strict and can have severe financial and legal consequences.
For important entities (such as machinery manufacturers), the most serious violations can result in administrative fines of up to €7,000,000 or 1.4% of total annual worldwide revenue.
Penalties for essential entities are even more severe.
Furthermore, liability extends beyond the employer to the entire company management. Under Article 23 of Italian Legislative Decree 138/2024, sanctions apply to those who:
1. approve the implementation methods for IT security risk management measures;
2. oversee compliance with obligations;
3. are responsible for violations under this decree.
Conclusions
All packaging technology suppliers must prepare for NIS 2 compliance, either because they are directly subject to the directive (as mid-size or large machinery manufacturers) or because they are involved due to supply chain obligations.
After completing an NIS 2 application assessment (Am I an essential or important entity or am I part of the supply chain of any such entity?), a minimal roadmap for implementation should include the following steps:
1. Conducting an initial gap analysis (What level of risk is my company exposed to in the event of a cyber incident? Are there any prevention and notification procedures in place? Do my products comply with industry standards? What is the level of security of my suppliers?).
2. Preparing administrative and management bodies (training, etc.) and establishing an internal organisational structure.
3. Preparing robust security measures (advanced firewalls, intrusion detection systems, data encryption, regular backups, etc.).
4. Technical measures for the supply chain (information flow traceability systems, adoption of contractual models, etc.).
5. Promoting cybersecurity awareness (staff training, incident reporting procedures, etc.).



















